How Secure is a VoIP phone system?
Updated: May 21st, 2025 | Published: May 12th, 2016
5 min read

We all know the internet can be a risky place. From malware and ransomware to phishing scams and spoofing attacks, it's natural to worry about the safety of any internet-connected service, including your business phone system. Since VoIP (Voice over Internet Protocol) operates over the internet, one of the most common concerns we hear from business owners is: "How secure is a VoIP phone system, really?"
Whether you're running a small business or managing multi-location operations, communication is at the heart of your success. Your phone system is more than just a tool, it's your connection to customers, vendors, and team members. Like every business-critical system, it must be protected with the same diligence as your email, financial data, and customer records.
At TeleCloud, we understand that trust in your communication tools is non-negotiable. That’s why we’ve built enterprise-grade security into our VoIP systems, so you can focus on serving your customers, not stressing over breaches, outages, or financial fraud.
In this guide, we’ll break down the most common VoIP security risks in 2025, show you how TeleCloud protects your system, and give you practical steps to safeguard your communications.
What Are the Common Security Risks for VoIP Phone Systems?
Like any other internet-connected technology, VoIP systems can be vulnerable without the right protections in place. Awareness is the first line of defense. Here are the most common VoIP-related threats in 2025:
1. Distributed Denial of Service (DDoS) Attacks
During a DDoS, malicious traffic floods your system with fake requests, overwhelming it and causing disruptions like dropped calls, busy signals, or degraded audio quality. This type of attack can render phone lines unusable and delay critical communications.
2. Toll Fraud
Cybercriminals exploit vulnerable systems to make unauthorized international calls, potentially racking up thousands in unexpected charges before being detected. Often, these attacks occur during off-hours, making early detection critical.
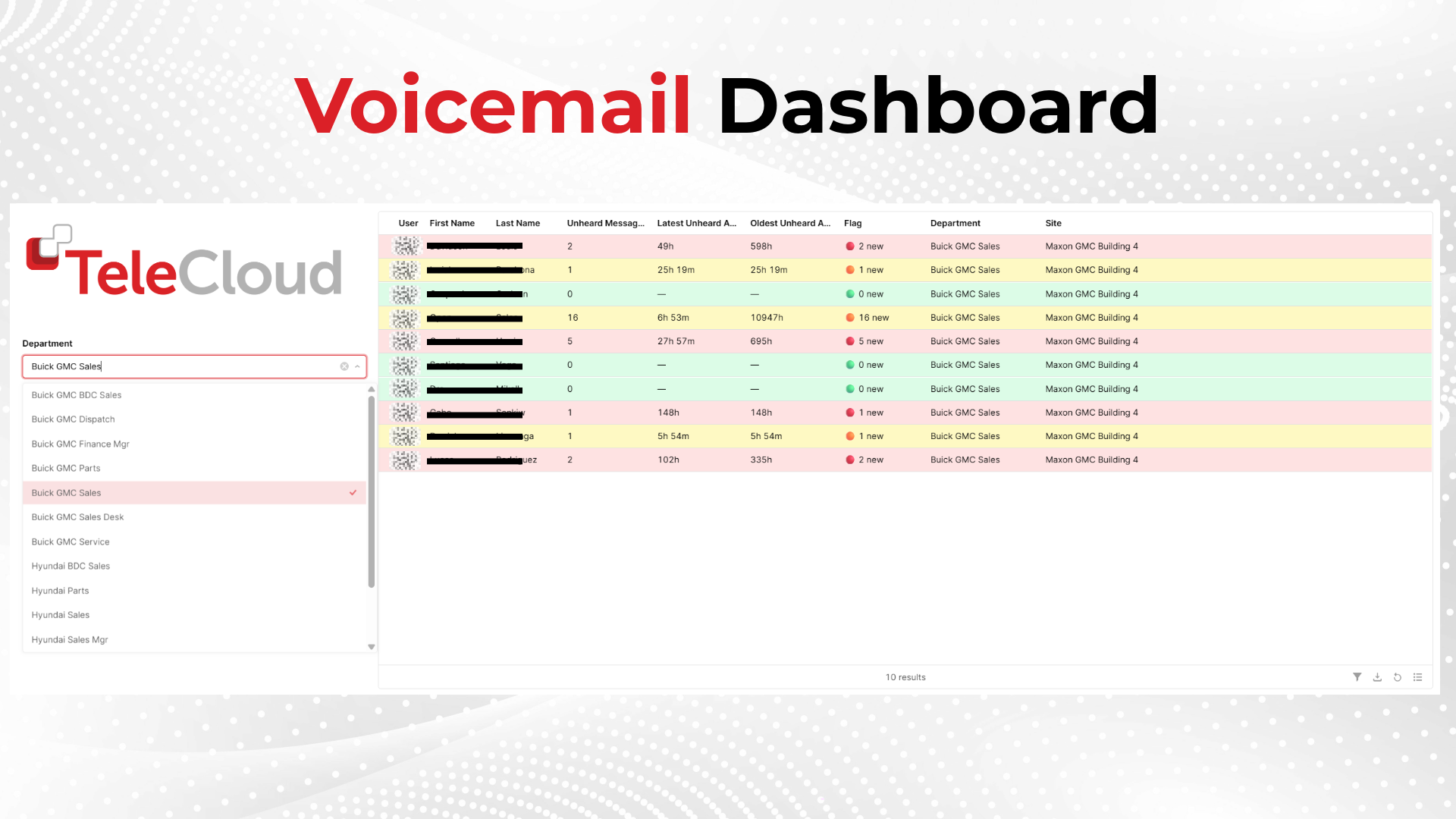
3. Voicemail Breaches
Weak or default voicemail passwords make it easy for hackers to gain access to confidential voicemails. This could expose sensitive information or create avenues for impersonation and further social engineering.
4. SIP Registration Hijacking
Attackers can override legitimate SIP credentials, redirecting or eavesdropping on calls without your knowledge. This compromises privacy and can lead to reputational damage if customer conversations are intercepted.
5. Vishing (Voice Phishing)
Bad actors impersonate trusted companies in phone calls to steal login credentials, payment information, or personal data, just like email phishing, but over the phone. These scams are becoming more sophisticated with the help of AI and caller ID spoofing.
6. Packet Sniffing & Interception
VoIP traffic can be intercepted if it's not encrypted properly. Without encryption, hackers can use packet sniffers to capture call metadata, voice content, or even login credentials. Secure Real-Time Transport Protocol (SRTP) encrypts the actual voice streams, while Transport Layer Security (TLS) protects the signaling and control information, ensuring end-to-end security for your communications.
How TeleCloud Secures Your VoIP System
Security isn’t a one-time setup, it’s an ongoing process. At TeleCloud, we take a proactive, multi-layered approach to VoIP security, using both technology and human vigilance:
1. Trusted Hosts
We restrict access to only authorized IP addresses and trusted devices, shielding your system from unauthorized intrusion and DoS attacks. This helps ensure that only verified users and endpoints can register and connect.
2. Smart Firewall Configuration
Unused ports are shut down, and essential ports are secured and continuously monitored. We also use intrusion prevention systems (IPS) to detect and neutralize abnormal traffic patterns before they escalate.
3. Strong Password Protocols
We enforce complex, unique passwords for every phone and voicemail box to thwart brute-force attacks. Administrators are trained on password rotation policies and credential hygiene, with recommended updates every 90 days to ensure credentials remain strong and secure.
4. International Call Restrictions
PIN codes and user-level access controls help prevent toll fraud by ensuring only authorized users can make international calls. You can also set geographic restrictions based on your business needs.
5. Real-Time Monitoring & Automatic Updates
We continuously monitor our systems for unusual activity using advanced analytics and threat detection tools. Our platform is automatically updated with the latest security patches, eliminating the lag time between threat discovery and resolution.
6. End-User Security Training
Employees are often the weakest link in any security setup. We educate your team to spot phishing attempts, use strong credentials, and avoid social engineering traps. We also offer refresher trainings as new threats evolve.
7. Data Encryption & Secure Protocols
All VoIP traffic is encrypted using SRTP and TLS protocols. This ensures that both call metadata and voice content are secured from end to end, even across public or remote networks.
8. Business Continuity & Redundancy
In the event of an internet outage or attack, our failover protocols ensure you remain reachable. We support automatic rerouting to mobile devices or alternate locations, minimizing downtime and customer impact.
Compliance Considerations and High-Security Industries
Security doesn’t just protect your systems; it helps your business meet critical compliance obligations. Many industries are subject to strict regulations when it comes to data privacy, call handling, and electronic communications.
Organizations in healthcare must comply with HIPAA, which requires voice systems that protect patient information through encryption and access controls. Financial services firms are expected to follow PCI-DSS and FINRA standards to prevent fraud and data leaks. Law firms, government contractors, and insurance providers often face SOC 2 or CJIS requirements related to system integrity and client confidentiality.
For these and other high-sensitivity industries, a VoIP system isn’t just a communication tool, it’s part of your compliance infrastructure. At TeleCloud, we design our VoIP solutions with security, traceability, and regulatory standards in mind. Our encrypted protocols, access management, and audit-ready systems help organizations confidently meet these demands.
Why VoIP Security is a Business Imperative
Security isn’t just about defense; it’s about ensuring business continuity, compliance, and customer trust. A compromised VoIP system can lead to more than just technical issues. It can damage your brand, erode client confidence, and create serious legal or financial exposure.
Whether you're a financial firm subject to compliance regulations, a healthcare provider managing PHI, or a local service business dealing with sensitive customer conversations, protecting your voice communications is no longer optional.
At TeleCloud, we stay ahead of the curve so you don’t have to. Our security-first mindset and constant vigilance help ensure your communications are protected, compliant, and always available when your team and customers need them most.
Ready to Protect Your Business Communications?
Don’t let security concerns keep you up at night. Schedule a free consultation with a TeleCloud expert and discover how we keep your phone system secure, reliable, and worry-free. Whether you’re switching providers or setting up VoIP for the first time, we’ll help you do it the right way from day one.
Commonly Asked Questions
Is VoIP secure enough for my business?
Yes, when properly configured and monitored, VoIP can be just as secure as traditional phone systems. With features like encryption, firewall rules, and continuous monitoring, a professionally managed VoIP system like TeleCloud offers enterprise-grade protection.
How can I prevent toll fraud and unauthorized calls?
Use PIN-protected international dialing, set up call restrictions, and ensure password hygiene across all devices. TeleCloud provides tools to block unauthorized usage and alerts for suspicious activity.
Can I use VoIP if I’m in a regulated industry like healthcare or finance?
Absolutely. TeleCloud supports HIPAA, PCI-DSS, and SOC 2 compliance requirements with encrypted communications, access controls, and detailed logs for audit-readiness.
What happens if my internet goes down?
TeleCloud includes business continuity tools like automatic call forwarding to mobile devices, failover routing, and cloud-based voicemail to ensure you're always reachable. Read More
Do I need special hardware to use a secure VoIP system?
No. VoIP systems can be used with desk phones, softphones (desktop apps), or mobile apps. Security depends more on the provider’s setup than on the hardware.
vin@telecloud.net OR call/text 908-378-1218